Three years ago, when I abandoned FogBugz after having used it for nearly 20 years, I landed on Help Scout, a fantastic support system offered by a company that seems to have a positive spirit and, cherry on top, is based locally to me in Boston.
There are few companies I’ve been as happy to spend money with. As a one-person support team, $22/month ($264 paid annually) gets me a reliable service that ticks all the boxes for my needs.
This simple pricing system was a breath of fresh air compared to many other services, which often require minimum user counts of five or more, have overly-complex user interfaces, or which seem unlikely to remain a going business concern.
Since I switched to Help Scout, I have been convinced that they are the best at what they do, and that I’d be in a real pickle if I were compelled to switch to anything else.
A Real Pickle
Over the past few weeks, many Help Scout customers have received notice that our plans will change to a new pricing model. Customers who haven’t received notice yet probably will soon. The new system is based on a rolling average of customer interactions. As they cleverly frame it: “the number of contacts you help each month.” Once notified, customers are granted six-months notice before the changes take effect.
The problem, for most Help Scout customers, is that the new system increases their monthly costs. A little for some, and a whole lot for others. The closest approximation to my current $22/month plan starts at $50/month and covers an average of 100 customer interactions per month. They’re obviously sensitive to the sticker shock this will produce, so they’re offering a two-year “Loyalty Discount” of about $20/month, reducing my monthly cost to $28.60/month. That’s still a 30% rise, but coming out to $6, it’s something I can live with.
For larger customers, the cost increase could be much worse. Imagine my company employed a three-person support team, handling customer interactions for 500 unique customers per month. Under current Help Scout pricing, I would pay $66/month. Exactly three times the amount I pay today. But under the new pricing structure, the minimum cost is $266/month.
How do you know which pricing tier you’ll fall into? Once you receive notice from Help Scout that your plan is changing, you’ll be able to see a graph of your recent customer interactions on a custom plan migration page within your account. For example, my graph shows that I fall comfortably into the 100 customers per month tier:
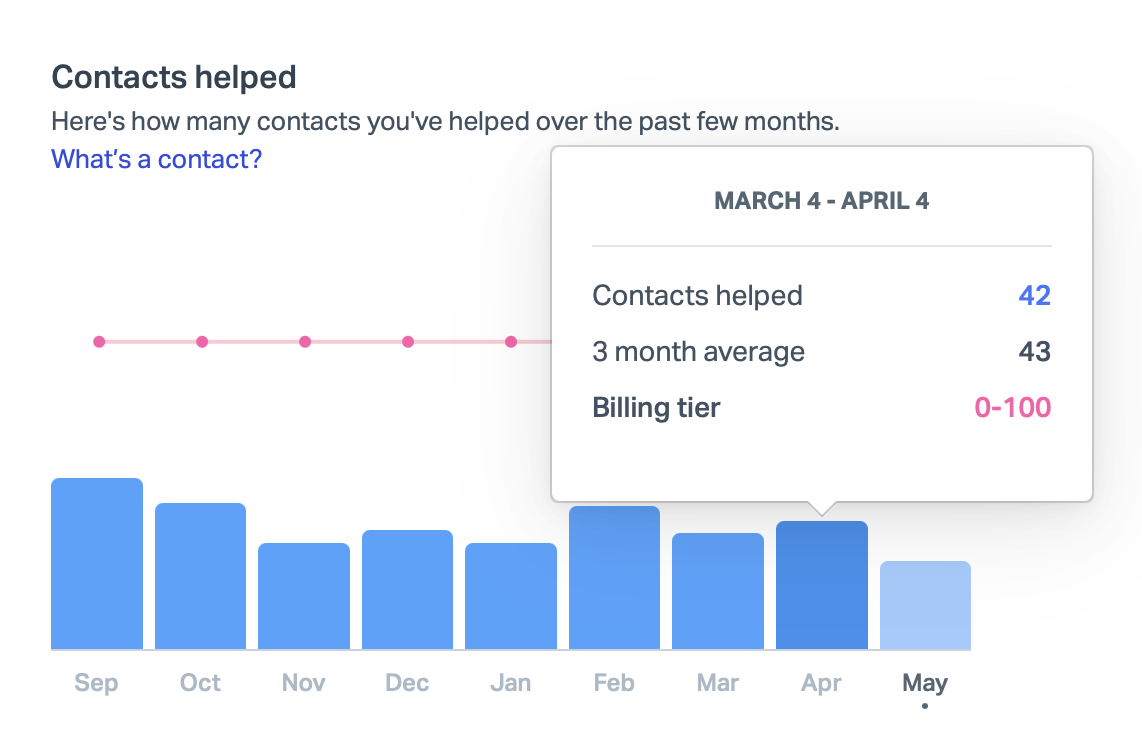
For new customers, they suggest for estimation purposes that the likely number of “customers helped” is around two-thirds the total number of emails you receive. So if you receive 150 emails per month, you might fall under the 100 contact tier, but if receive 200 emails per month, you most likely do not.
The Upside
The new pricing will benefit some customers. A brand new “Free” tier is a fantastic option for new customers who assist fewer than 50 customers per month on average. I fall into this range, so I wondered if this option might suit me. I contacted Help Scout and they agreed that I qualified for the plan, with the exception that I was using more than maximum 100 “tags” included in the free tier. I tag some Help Scout issues with GitHub ticket numbers, but if I were willing to delete some tags, I could switch immediately and start paying $22 less per month than I do now. That’s tempting, but the big problem with the free tier is that it removes access to the Help Scout API, and the ability to “Export” your data. Restricting data export is very 2005, and I wonder how it will play out in Europe.
It’s also possible to imagine customers with a large number of agents assisting a relatively small number of customers. For example, if my imaginary three-person support team handled only 100 unique customers per month, the monthly cost would go down with the new pricing, from $66/month to $50/month. Or $30/month if they provide the same loyalty discount, but I suspect for customers positively affected by the price change, there will be no such discount.
Finally, customers who lean heavily on Help Scout’s AI features might see savings. Currently, customers who want to use these features have to pay at least $44/month per user, twice the standard plan. I wouldn’t know and don’t care how much these savings might be, because although I am not opposed to AI in general, I don’t appreciate or employ it in the context of customer support.
What To Do?
For a customer in my particular position, whose monthly price will go up by $6, the easiest way forward is to do nothing. I’ll keep enjoying the same glorious product I have enjoyed for the past three years, at only a slightly elevated price. After another two years, we’ll see how things shake out. I contacted Help Scout about the “loyalty discount” and what happens when it expires, and they assured me that they would “do something” to keep people in my situation from seeing too much of a price hike. They claim to be aware of a problem there, but just aren’t sure how to manage it.
For customers who will see a more painful increase in cost, as with the $66 to $266 spike I contemplated above, I have to imagine they will consider other options. While I maintain that Help Scout is the best at what they do, there are, of course, alternatives. I haven’t made a thorough evaluation lately, but my pal Paul Kafasis shared a list of potential options put together by Rogue Amoeba’s Support Manager Chris Barajas. You might stumble upon something you like while perusing these:
That last option, FreeScout, is notable for being open source. Another option that came across my radar is a system called Zammad, which offers full-service hosting with the same refreshingly-simple “per user” pricing I once admired Help Scout for. And like FreeScout, Zammad is also open source. This means that either of these options can be self-hosted on your own server, akin to hosting your own WordPress installation.
I don’t relish the idea of maintaining my own help desk, but with the ever-looming threat of changes in functionality and pricing, for such a critical piece of infrastructure, I am considering it. With the wide-spread adoption of technologies like Docker, which bundle software into self-contained, easily-deployed packages, and services from companies such as Amazon, Microsoft, and Google, which make it easier to host such packages, it has never been easier to maintain a “self-hosted”, yet highly reliable web service.
Takeaway
While I respect Help Scout’s right and responsibility to manage the destiny of their own business, I think they are making a mistake with these changes.
It’s one thing to assert that they are upsetting their current user base. I think they are, but worse, I think they will turn off prospective users as well.
People don’t like fluctuating prices. Businesses especially don’t like fluctuating prices. With Help Scout’s old business model, it was very easy to understand what you were paying for, and what you would receive. The new system requires work simply to determine if pricing is viable, let alone practical. And once you’ve settled into a tier, you run the risk of being “punished” for helping more customers. The idea that I might one day consider whether to help a customer today, at the cost of sending myself into a higher pricing tier, or helping them tomorrow, and saving a bit of cash, makes me both frustrated and a little sick.
I suspect that very-large companies will find these changes the most palatable. Not only because at greater scale the pricing is more predictable, but because larger companies have far more expenses, many of which probably dwarf the cost of their Help Desk software. The smaller the company, the more likely Help Desk software is to be one of the main monthly expenses.
In a private chat, somebody suggested to me that small-time companies like mine are not Help Scout’s target market. That might well be true, but if it is, I think that is also folly. Most companies with 10, 100, or 1000 customer support agents started as companies with 1, 2, or 3 support agents. Help Scout’s new “Free” tier is a nod to the importance of luring in customers when they’re small and have little money to spare. They just seem to drop the ball a bit when it comes to taking care of customers at slightly-more-successful levels.
I am not sure what percentage of customers have been notified so far, but the number seems to be accelerating. I suspect the amount of negative feedback Help Scout receives will also accelerate. Hopefully this will inspire changes that make this transition more palatable for everybody.